Mesh networking on OpenWRT 15.05 with OLSR: Difference between revisions
| Line 21: | Line 21: | ||
=Setup a Node= | =Setup a Node= | ||
This is for setting up a simple node that has no access to the outside but can connect to other nodes. Most unit in the network will have this configuration. | This is for setting up a simple node that has no direct access to the outside www but can connect to other nodes. Most unit in the network will have this configuration. | ||
We will use here | We will use here | ||
Revision as of 22:23, 25 July 2018
Overview
This guide covers configuration of OpenWRT to create a mesh network based on OLSR.
Preliminaries
Access with command like via ssh is required. Use Putty or any other terminal.
Software
OpenWRT 15.05 Chaos Calmer is installed with defaults. Target device has 8Mb flash memory minimum.
Hardware
This will work on EmonWRT3 and ModWRT devices.
If using WR703N router it must be modified with upgraded flash memory. The default unit does not have sufficient memory.
Setup a Node
This is for setting up a simple node that has no direct access to the outside www but can connect to other nodes. Most unit in the network will have this configuration.
We will use here
- Wired - Static IP 192.168.2.1 (for configuration access only)
- Wifi - Ad-hoc wifi with Static IP 10.10.10.xx (for comms with other nodes).
-1- Install packages
Install the required packages with the command below:
opkg update opkg install luci-app-olsr luci-app-olsr-services luci-app-olsr-viz luci-lib-json opkg install olsrd olsrd-mod-arprefresh olsrd-mod-bmf olsrd-mod-dot-draw olsrd-mod-dyn-gw olsrd-mod-dyn-gw-plain olsrd-mod-httpinfo olsrd-mod-mdns opkg install olsrd-mod-nameservice olsrd-mod-p2pd olsrd-mod-pgraph olsrd-mod-secure olsrd-mod-txtinfo olsrd-mod-watchdog olsrd-mod-quagga opkg install wireless-tools
-2- Setup Wired LAN
Make sure the wired interface LAN is setup with static IP address. For our example we will use 192.168.2.1 (if you opt for another ip address then avoid the internet access subnet - like 192.168.1.0 for home routers.)
Make sure the interface is not bridging the wifi.
- In Network | Interfaces click on Edit on the LAN interfaces. Then in Physical Settings untick create a bridge over specified interface(s).
- Make sure Ethernet Adapter: "eth0" (lan) is ticked on.
You should now configure this unit by connecting a computer directly to this node with an ethernet cable.
The Lan interface should look like this below.

-3- Setup wifi mesh interface
Go to Network | Wifi click on Edit on the only wifi interface that should be there.
Down the page setup the following:
ESSID: OLSR
Note: ESSID must be the same on all nodes.
Mode: Ad-Hoc
Network: tick create and enter 'mesh'
The wifi interface should look like this below:

If the wifi interface is disabled enable it clicking on Enable.
Go to Network | Wifi click on Edit on the interface MESH.
Setup these parameters below:
Protocol: Static address (click the Switch Protocol button now).
IPv4 address: 10.10.10.2
Set IPv4 address above as 10.10.10.x with x being the number of your node. 2 in our example here.
IPv4 netmask: 255.255.255.0
Use custom DNS servers: 8.8.8.8
Go to Firewall Settings tab.
Tick on unspecified -or- create: and enter 'mesh'
click
![]()
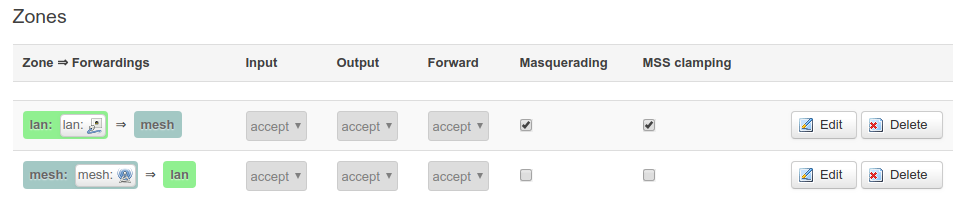
-4- Setup Firewall
Go to Network| Firewall.
Find the Zones section at the bottom of the page.
Remove any entry that concern WAN.
For entry mesh choose Forward as accept.
click
![]()
-5- Setup OLSR
Go to Services | OLSR IPv4.
Select tab Plugins.
Tick on olsr_jsoninfo.so.0.0.
click
![]()
Go to Services | OLSR IPv4.
Find the Interfaces section at the bottom of the page.
Click on the Edit button of the only entry that is there.
For parameter Network Select entry mesh.
click
![]()
-6- View Connections
Go to Status | OLSR The page will show the number of interfaces and neighbours.
Setup the Gateway - Node with internet access
Setup the device as a normal node as described above.
Go to Services | OLSR IPv4.
Select HNA Announcements tab.
Click Add.
Enter:
Network address: 0.0.0.0
Netmask: 0.0.0.0
click
![]()
Go to Network | Firewall
Find Zones at the bottom of the page.
Click on Edit for lan.
Tick on Masquerading.
Tick on MSS clamping.
Find the Inter-Zone Forwarding at the bottom of the page.
Tick on all Allow forward to destination entries.
click
![]()
Firewall zones should look like this below.
Wifi Encryption
opkg remove wpad-mini opkg update opkg install wpad authsae